If you work in IT, you’re probably no stranger to Mobile Device Management technology. Mobile Device Management Platforms, or MDMs for short, are typically used by businesses to manage the following tasks from a single, centralised location:
- To deploy or retire devices
- Remote wipe or disable a lost or stolen device
- Easily roll out of updates or applications to the mobile estate
- Keep asset list of company mobile devices
When I’m taking to customers, I ask one simple question: Wouldn’t it be easier to simply manage your mobile devices – including your company laptops- from within your Microsoft 365 ecosystem?
This is where Microsoft Intune comes in.
Microsoft Intune is a cloud-based mobile device management (MDM) and mobile application management (MAM) platform for your apps and devices. It is now directly part of the Microsoft Endpoint Management suite of applications, which we have covered in a separate blog post. If you want to understand a bit more about Microsoft Endpoint Manager, click here to be taken to the relevant place.
Microsoft Intune lets you control features and settings on Android, Android Enterprise, iOS/iPadOS, MacOS, and Windows 10 devices – while also integrating with other services, including Azure Active Directory (AD), mobile threat defenders, ADMX templates, Win32 and custom LOB apps, and more.
Intune allows for complete global management of the mobile device estate. Devices can be wiped remotely if needed and access can be restricted for devices that have been lost or stolen. With Intune, you can also provide a self-service company portal so users can enrol their own devices and install company applications. This gives the company visibility and control over what apps are being installed, without compromising on the user experience.
Intune also gives you complete control over how your company devices are used, including mobile phones, tablets, and laptops. You can configure specific policies to control applications. For example, you can prevent emails and documents from being sent to people outside your organization, ensuring they never fall into the wrong hands. Intune also allows people in your business to use their personal devices for school or work. On personal devices, Intune helps make sure your organization data stays protected, and can isolate organisation data from personal data where necessary.
In Intune, devices can be managed using an approach that's right for your organisation. For company-owned devices, you may want full control on the devices, including settings, features, and security. With this approach, devices and users of these devices enrol in Intune. Once enrolled, they receive your organisation’s pre-set rules and settings through policies configured in Intune. For example, you can set password and PIN requirements, create a VPN connection, set up threat protection, and more.
Other actions can be executed by Admin Rights users remotely, such as password resets, device locking, data encryption and a full device wipe to protect company data on lost or stolen devices. You can also restrict access to certain applications on any unenrolled or non-compliant devices.
For personal devices or bring-your-own devices (BYOD), users may not want their organization administrators to have full control. With this approach, users can be given options. For example, users can enrol their devices if they want full access to your organization resources. Or, if these users only want access to email or Microsoft Teams, then they can use app protection policies that require multi-factor authentication (MFA) to use these apps.
As the Microsoft diagram below shows, Microsoft Intune can be a central hub for full management, deployment, and controls of all your company mobile devices.
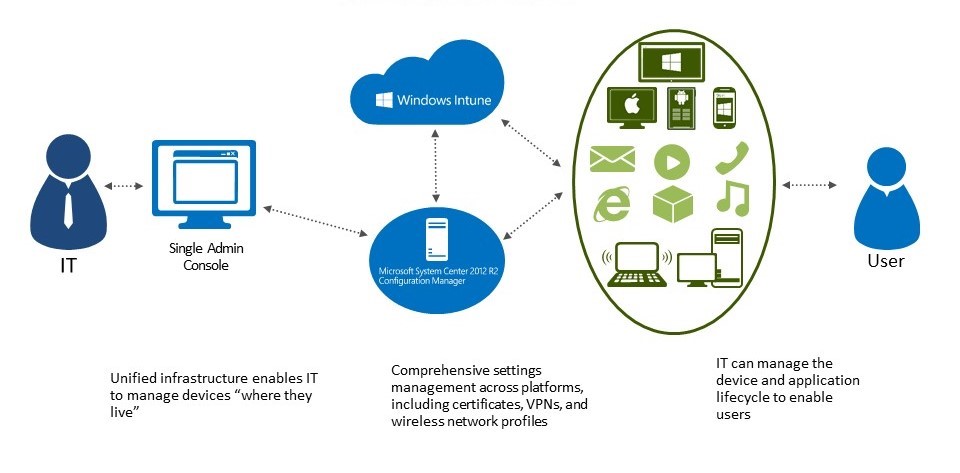
When devices are enrolled and managed in Intune, administrators can:
- See the devices enrolled and get an inventory of devices accessing organization resources. This is particularly useful for those organisations who are required to have an inventory of assets to meet ISO27001 standards, as the inventory in Intune is always updated, showing the correct data in real time.
- Configure devices so they meet your security and health standards. For example, you probably want to block jailbroken devices.
- Push certificates to devices so users can easily access your Wi-Fi network, or use a VPN to connect to your network.
- See reports on users and devices that are both compliant and non-compliant.
- Remove organization data if a device is lost, stolen, or not used anymore.
- Push company applications out from a central location
To conclude, many organisations benefit from having a Mobile Device Management technology. Intune gives you the capabilities you require from other MDMs with added extras, benefiting from its natural compatibility with other products in your Microsoft estate.
What's Next?
If you want to find out more about how Microsoft Intune works on a Technical level, it's worth checking out the recording from our recent webinar. Click Here to go straight there.