Microsoft Intune Policies that can Improve Security
In my recent blog How to Improve Office 365 Security, I mentioned how the Microsoft 365 product suite is perfectly suited for our new flexible approach to working. It gives employees what they need to access key company information and applications from any location and on multiple devices. Although this is a positive, it does introduce new security challenges.
Microsoft have developed tools within the Microsoft 365 product suite to mitigate these new risks. They do this without removing or reducing the benefits around mobility.
One of the three key Microsoft 365 products I mentioned in my previous blog was Microsoft Intune. I am going to look at Microsoft Intune in more detail here, giving you some practical take-aways that you can implement into your security strategy.
A Quick High Level Overview…
As I mentioned in my last blog, Microsoft Intune is a cloud-based computer management, mobile device management (MDM) and mobile application management (MAM) platform for your organisation’s apps and devices. I am going to focus on MDM and MAM in this blog post.
Microsoft Intune allows you to control features and settings on a range of devices, including Android, Android Enterprise, iOS, MacOS. However, the true power of Microsoft Intune comes into play when managing the security of the devices within your organisation. That’s why, rather that focus on the general management elements of Intune, I am going to sharpen the focus on how the product can be used to improve your security.
Using Microsoft Intune to Improve Security…
It’s worth pointing out some of the more broad-stroke security benefits of using Mobile Device and Application Management tools such as Microsoft Intune. They give organisations the ability to manage the following tasks from a single, centralised location:
- Deploy or retire devices
- Remote wipe or disable a lost or stolen device
- Keep an asset list of company mobile devices
But I want to be a little more specific than this by looking at how powerful Intune can be when used in conjunction with Conditional Access to manage the application of Multi-Factor Authentication.
Before I go into it, it’s worth reiterating the importance of Multi-Factor Authentication (or 2FA, as you may know it as). A recent Microsoft publication highlighted the following:
- 300,000,000 Fraudulent Daily sign in attempts
- 81% of breaches are caused by credential theft
- 73% of passwords are duplicates
A more striking statistic however, is that 99.9% of the above can be blocked with MFA! So that does beg the question- why aren’t more organisations enforcing it?
There are various answers to this question but the common factor between them all is that it’s perceived as annoying and inconvenient. When implemented using an ‘on’ or ‘off’ approach that’s available in basic Microsoft 365 packages, I can definitely sympathise with this criticism. It’s easy to see why being asked to enter a code every time you need to log back into your device becomes a hindrance. But this is where Intune and Conditional Access solves a genuine problem.
During our Microsoft 365 Managed Service onboarding, Circle Cloud implement an Intune Policy that creates the rules for a ‘Compliant Device’. We ensure that fundamental security principles, such as password complexity and OS version, are detailed, monitored, and rolled out to all your company owned devices centrally from Microsoft Intune. Once these parameters have been set, it’s easy to see in the Microsoft Intune portal which devices are ‘compliant’ and if not, why not.
I have provided an example Microsoft Intune policy we use for company devices below:
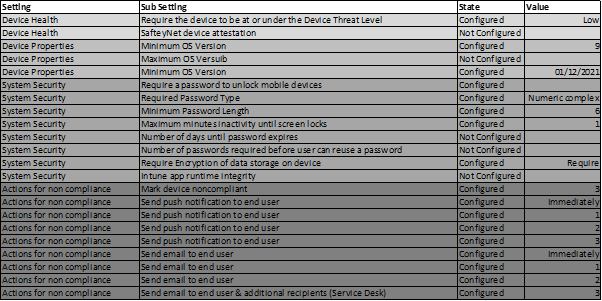
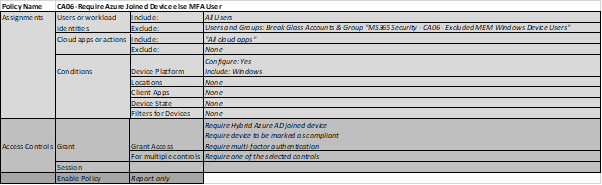
So what does Conditional Access have to do with it? Well, once you’ve defined what a ‘Compliant Device’ looks like using Microsoft Intune (see above), you can create a Conditional Access policy that assesses all connection attempts to your tenant against the ‘Compliant Device’ standards. To put simply, if somebody logs into a device, Conditional Access will check whether it’s ‘compliant’ in the Intune portal. If it is, access will be granted. If not, you can enforce MFA. Doing this means that there is a more sensible approach to how MFA is applied to users, making it much more likely to successfully adopted in your organisation.
Here is an example of a Conditional Access Policy we use. Notice in the ‘Access Controls’ section there is a stipulation called ‘Require device to be marked as compliant’.
What about Personal Devices?...
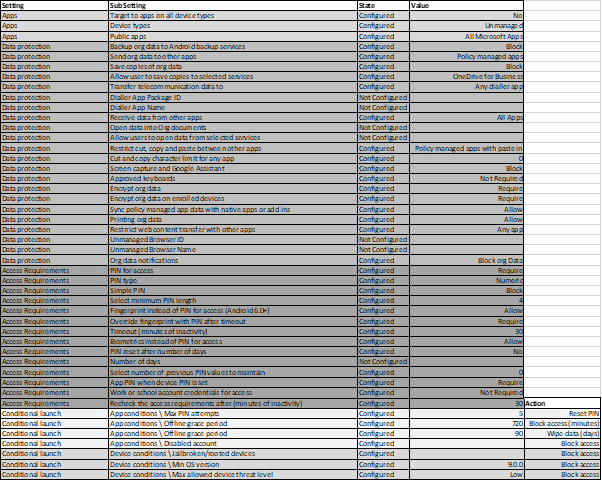
The above refers to scenarios for devices that are owned by your organisation. However, if your company has a BYOD policy, you’re probably wondering how this would look. The big challenge with security on personal devices is that it’s way too intrusive to expect to manage somebody’s full device. This is where Microsoft Intune’s Mobile Application Management comes in.
Mobile Application Management allows you to apply a security layer in front of the application rather than the device. This means that you user can use their mobile phone exactly as the please, however they will be asked to provide credentials should they attempt to access a company application.
Here is an example Microsoft Intune policy for BYOD scenarios. As you can see, you can restrict copying and pasting from company applications, as well as encrypt the organisation’s data when being used on a personal device.
Conclusion…
Microsoft Office 365 is enabling our workforces to work effectively from anywhere. Doing so is posing some security challenges, but there are none that can’t be overcome by using the facilities available within the Microsoft product suite. Microsoft Intune is such a powerful way to set and maintain compliance standards for the mobile devices in our organisations. When configured in conjunction with Conditional Access, as demonstrated in this blog post, we can take huge strides towards closing some of the security gaps we’re faced with in this age of remote working.













