In our example scenario the account credentials were compromised, and they were used to log in from an external attacker. What we need to think about first is how could we have protected the account so that it couldn’t be accessed externally.
We have covered the easiest way of protecting an account under the Mitigate section – Multi Factor Authentication- however, for this post I will be addressing user inconvenience, the most common complaint that comes with this measure.
When introducing the idea of MFA into your Organization, the most common complaint you will get is that it takes more time and is an inconvenience for end users given that they are required to use it each time they login to Office 365 or associated application. When looking at an organization that requires MFA, my first suggestion is always Conditional Access. This is a feature included in the Azure AD Premium P1/2 packages and is available as part of the Enterprise Mobility Suite.
Conditional access gives the protection of MFA whilst also using controls that reduce the intrusiveness for users. In this post I will demonstrate the Locational Based Conditional Access which allows you to define which locations you would like your users to be exempt from MFA e.g. secured head office, company remote VPN. To access your Conditional Access settings, from the Azure Management portal go to: Azure Active Directory > Conditional Access.
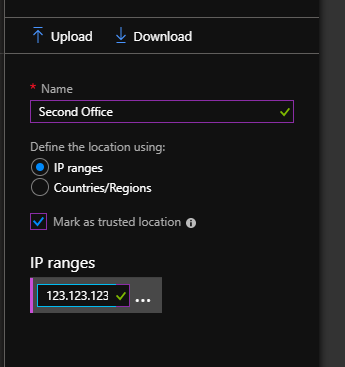
We will start by creating our Named Locations, open the Named Locations Blade and click New location, from here we can add a location and its IP range. See below for an Example:
Start by creating a New Policy. In my example I have called this MFA_Enforce, under users and groups I have applied this to All Users. Under Cloud Apps I have selected All cloud apps.
The next section is Conditions. This is where we set the conditions of the policy- for my conditions I have chosen to include Any Location and Exclude All Trusted Locations. We then add the access control, allowing access but requiring MFA as seen below:
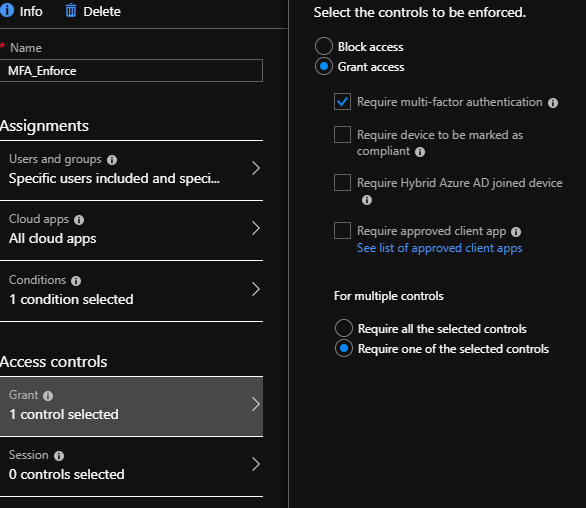
We have now set up a conditional access policy. This policy applies the following rules:
User working inside the office: Do not Prompt for MFA
User working outside of the office: Enforce MFA
This preventative measure brings MFA protection whilst excluding the trusted IP of the Office WAN, therefore not impacting users within the Office.













