In this four-part blog series, I will be exploring the options that System Administrators can take to protect their organizations during the current extreme threat level of cyber attacks. The most common attack vector witnessed is through Exchange/Email. Having a clear strategy and set of measures in place is crucial for your organization’s security.
I will break this post down into four areas:
- DETECT
- MITIGATE
- PROTECT
- PREVENT
I will be looking at these steps from the perspective of an organization that doesn’t have any real technical measures in place or could use a review of their current systems.
Scenario
For this Article I will be examining the common scenario of a user credential breach. We will assume the following variables for the environment:
- All users using Office 365 for Email/Sharepoint
- Using On-Premise Active Directory for Asset/User Management – ADConnect in Place
In our example the user has entered their details into a fake form from a Phishing email which looked to originally be from their manager. These details have been picked up by the 3rd party and used to log in externally to the organization. We have detected this using the Microsoft CloudApp Security Platform.
Phishing Part 1: Detection
One of the most crucial components of a well secured network is breach detection. Being able to detect a breach as soon as it happens allows you to start mitigating before more damage can be done. For breach detection, in this scenario, we are making use of Microsoft CloudApp Security with notifications. CloudApp Security comes with plenty of built in features that can be used to detect breaches. In this case we received alerts from the “Impossible Travel Activity” and “Activity From an Infrequent Country” alerts. See below for an example of these:
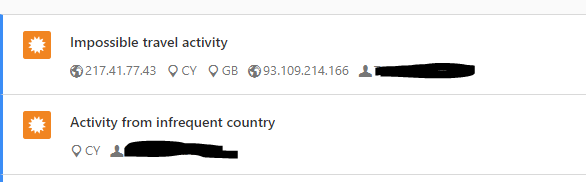
Once these alerts were triggered a notification was sent to our support mailbox. This process can be set up for any of the built-in alert types, see below:
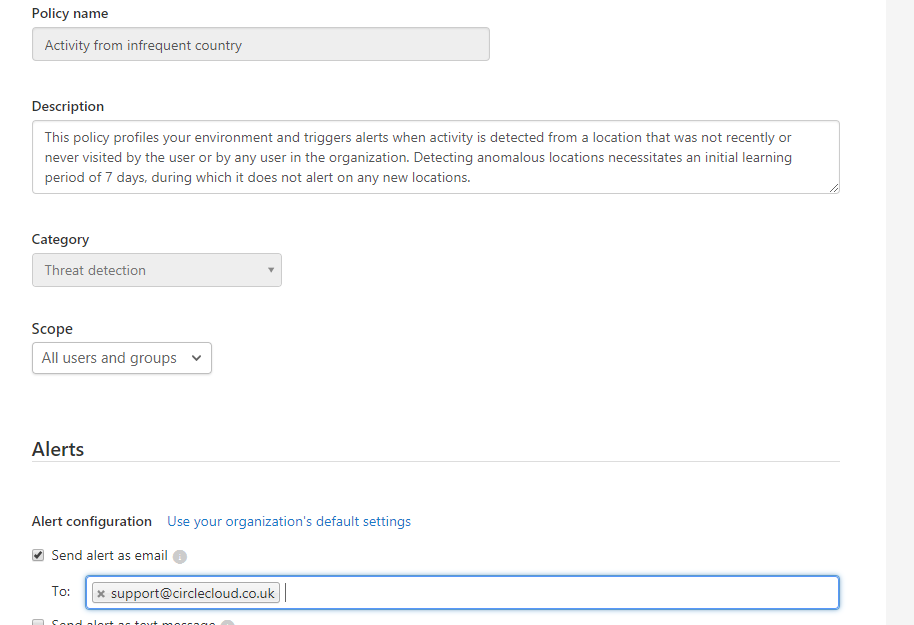
This then allows us to check if they are legitimate or someone accessing the account unauthorized. For our example scenario we will assume that this user is not abroad.
Once we have qualified this alert we will move on to Mitigating the threat.













